The Different Types of Malware, and What You Should Look Out For
Viruses, spyware, malware – it seem’s like they’re everywhere these days. In our computers, our phones, even hiding in the credit card swipers down at the local Target store. The internet can be a scary place, filled with criminal masterminds who might try to steal your banking information, delete all your iCloud photos, or take your hard drive ransom for cold hard cash. So with all these threats waiting just over the horizon to strike, how can you know exactly what to look out for when browsing and sharing your life online?
In this four-part series, we at PCMech are going to give you a rundown of all the biggest infections that are trawling around the net today, as well as a slew of step-by-step guides on how you can better protect yourself and your family from clicking the wrong link or downloading one too many dodgy files.
Malware
When you talk about “malware”, you talk about a lot of things.
Colloquially malware is a broad term for the dozens of different types of infections you can get on your computer. Spyware is sometimes miscategorized as malware (adware too), but all in all the general definition rests around the concept of “a program or virus that sneaks into your computer, and does a bunch of stuff you don’t want it to”.
It’s an umbrella term that covers many of the other variants we’ll talk about in this article, but can also be classified as its own, independent threat. Trojan horses, rootkits, backdoors and viruses on your hard drive can all equally call themselves malware, but so can the program that cost the banks $45 million in cash stolen straight from the mouths of their own ATMs.
So what is “malware”? Well, read on to find out.
Adware
First up in the queue of questionable downloads, we have adware.
Of the various infections listed here, adware is easily the most innocent of the bunch, (not that this makes it any less annoying, of course). Generally adware is delivered to computers through third-party software installations, asking “If you want to install the Yahoo! toolbar in your browser”, or “Check this box to set Bing as your homepage”.
Stuff like search toolbars, sponsored “PC Cleaners”, and new homepages that try to squeeze their way into your machine on the back of something you actually needed are a plague in the industry. Thanks to one big legal loophole, by clicking “yes you can install this” in the original setup, technically you’re giving whatever company owns that software permission to collect information on whatever you or your loved ones do on that system.
Most of the time the downloads are innocuous, only being used by ad companies in bulk to log information like what websites you’ve visited in order to use it later for marketing purposes. Very little (if any) identifying information is scraped into their archives for long term storage, however it can become a real problem if too much of it stacks up in your computer. An influx of adware can cause everything from minor performance losses to catastrophic failure of the OS, so even though it may be the least worrisome of the virus variants, it’s still always a good idea to opt out of any installations you don’t recognize from the start.
Spyware
Spyware is where things start to get a bit nastier. In simple terms; think of it as though adware teamed up with Russian mobsters, and instead of advertising information, it was trying to steal your bank account and all the money inside.
Spyware is a style of malware that doesn’t attempt to harm or hinder your computer in any way, and in fact is usually designed to achieve exactly the opposite response. See, spyware does just what the name implies, sitting back in the shadows of your PC while it gathers information and waits for the moment that you decide to shop for something online without running your antivirus software first. All it needs is to keylog one credit card, and then it’s off to the races emptying all your accounts as fast as possible before any fraud detection services are activated.
More often than not, these types of infections will burrow themselves inside the ad content of clandestine websites like illegal video streaming portals and torrent lists, as well as torrented software and movies. These networks make the perfect breeding ground for spyware, due to the type of customers that find themselves stealing movies instead of paying for them.
Unfortunately because of the nature of the virus, finding out if you’ve been infected with spyware is one of the hardest tasks that anti-malware software struggles with today. Spyware doesn’t need to be seen or heard, it just has to read everything you type and take what it wants whenever the time is right.
Phishing
Although it’s spelled a bit differently, “phishing” attacks are almost exactly what they sound like: hackers leading out some kind of line to unsuspecting internet users, hoping that one of them will eventually take the bait.
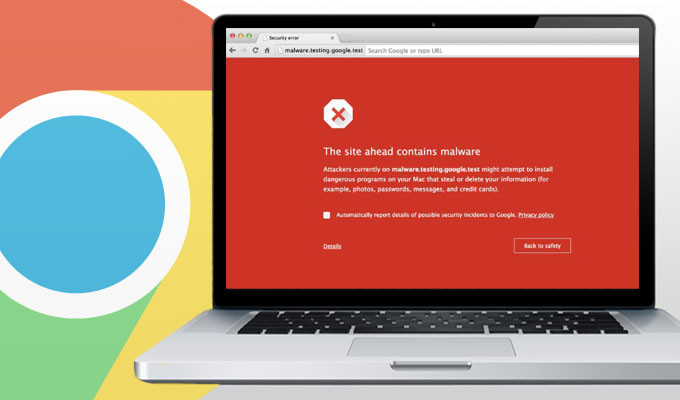
The scam works by creating falsified links that on the surface look like they’re being directed to reputable websites like Facebook or your email account. In reality, these pages are made by hackers to seem nearly identical to the page they’re supposed to be imitating, and are designed to steal your login credentials once you type them into their site.
Luckily, these days most major browsers have phishing prevention settings and software built in, including Chrome, Firefox, Safari, IE and Opera. If you click on a suspicious link in your email or navigate to the wrong page from Google, the browser will automatically flash a warning that prevents you from getting to the page, generally with a prompt that looks something like what we see above.
Phishing attacks are usually just a fraction of the business for a lot of underground hacking organizations, namely because the vector they rely on to get through to your computer also happens to be one of the best defended areas of any vulnerable network. But, just because phishing isn’t paying the way that it used to doesn’t mean that hackers aren’t still finding new ways to rake in the dough…
Ransomware
This is the big one. The one that no one saw coming, the one that caused the loss of petabytes of valuable data across tens of thousands of computers, and the one that continues to wreak havoc even to this day: ransomware.
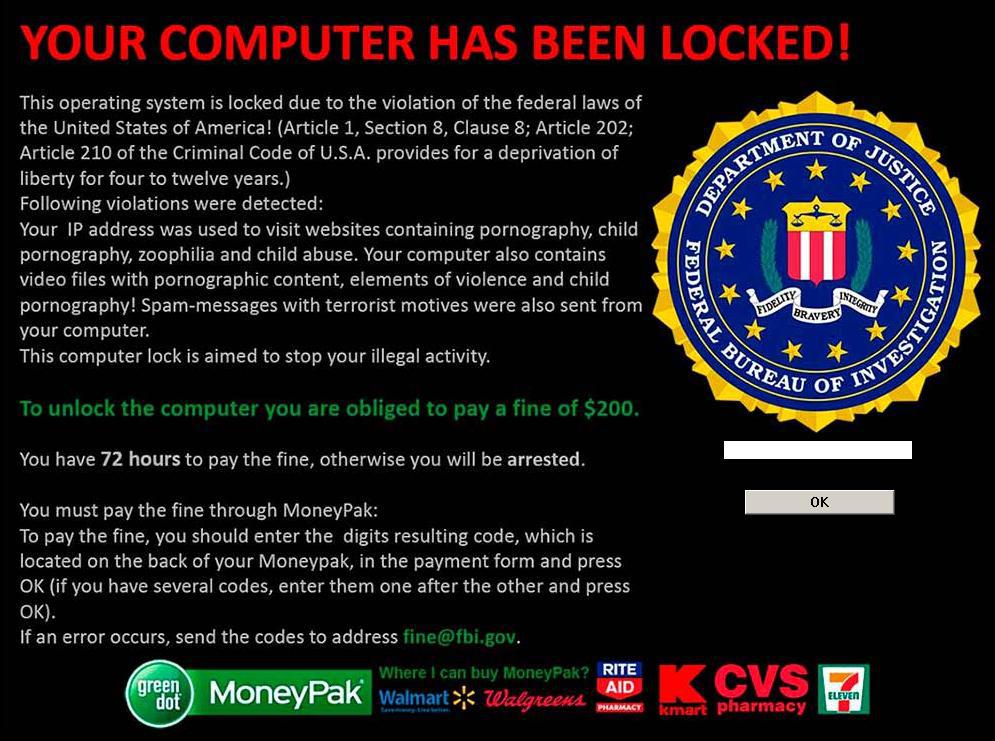
Ransomware, like phishing, is pretty much exactly what it sounds like from the get-go. The virus works by travelling over regular traffic routes (bad links, email scams, drive-by downloads, etc), and then installing itself on the master boot partition of your computer or mobile phone. Once it detects the user is away from the device for more than an hour or so, it locks the entire device from the BIOS, and encrypts all the data contained within in an instant.
By encrypting the hard drive from the master boot partition, the ransomware will hijack your machine to the point of being completely non-functional, other than the ability to display a simple image and connect to a Bitcoin marketplace. The idea is that by threatening to delete all your data, the hackers can pressure users into paying hundreds, even thousands of dollars at a time just to get it back.
That’s right; if you get infected with ransomware, one of the only ways to regain access to your data is to pay the hijackers however much they’re asking for in Bitcoin within 24-hours, or face the possibility of having all their family photos, important tax documents, and music collection wiped on the spot. Of all the infections we’ve mentioned in this article, this is the one that you’ll know you have the second you’re attacked. Ransomware wants you to know its there, because the threat it’s making is real, tangible, and on a clock.
Because ransomware is so new, preventing its spread has proven to be a losing game for the whitehats in the industry. As such, the only true way to recover from a ransomware attack is to remove the power it has over your machine in the first place. If you use an offline, air-gapped hard drive to backup all your most valuable data on a daily basis, no matter when the ransomware hits, you’ll already have a fresh version of your PC ready to boot into once the 24-hour limit passes.
So, now that you know about all the different kinds of malware and what to look out for, we’re going to help you create a personalized security strategy that works best for you and your home network.
Stay tuned, as in the next part of this series we break down the tips, tricks, and tools you’ll need to prevent yourself from getting infected, as well as a detailed guide on what you should do if your computer is being bogged down by someone else’s secretive software.
Image Credits: Google, FBI.gov, Flickr/Robbert Steeg, Flickr/Lee Davy, Pixabay
















One thought on “The Different Types of Malware, and What You Should Look Out For”